In an increasingly interconnected world, the desire for privacy has become paramount. We navigate a digital landscape where our every click, search, and interaction leaves a trail, often collected, analyzed, and potentially exploited. In response to these pervasive surveillance concerns, many individuals have turned to Virtual Private Networks (VPNs) as a shield, a digital cloak promising anonymity and security. The allure is understandable: a simple click connects you to a remote server, masking your true IP address and encrypting your internet traffic, seemingly rendering you invisible to prying eyes.
For a time, VPNs were hailed as the quintessential privacy tool, a digital panacea for those seeking refuge from the watchful gaze of governments, corporations, and malicious actors. Marketing campaigns painted a picture of impenetrable tunnels, safeguarding your online activities from interception. The reality, however, is far more nuanced and riddled with potential vulnerabilities, turning this seemingly secure solution into a potentially leaky and ultimately unreliable shield for true anonymity.
The False Promise of VPN Anonymity:
Sponsored
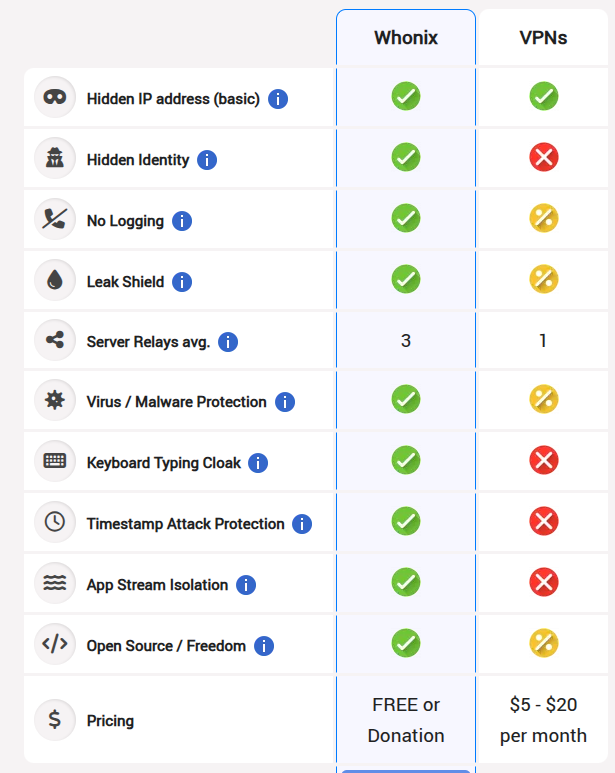
The inherent limitations and potential pitfalls of relying solely on VPNs for robust anonymity are numerous and often underestimated. While they offer a degree of privacy by obscuring your direct IP address from the websites and services you access, they fall short of providing the comprehensive anonymity many users believe they are achieving.
One of the most significant vulnerabilities lies in the fundamental trust placed in the VPN provider itself. You are essentially routing all your internet traffic through their servers, granting them a privileged vantage point into your online activities. While reputable VPN providers often boast strict “no-logs” policies, these claims are not always transparent or verifiable. History is replete with instances where VPN providers have been compelled by legal authorities to hand over user data, or worse, have been found to be logging and even selling user information themselves. The jurisdiction in which the VPN provider operates is also a critical factor. Governments in certain countries possess the legal authority to demand access to VPN server logs, effectively negating any perceived anonymity.
Furthermore, even with encryption in place, the connection between your device and the VPN server is still susceptible to certain types of attacks. Metadata, such as connection timestamps and the amount of data transferred, can sometimes be exposed. Additionally, vulnerabilities in the VPN software itself can be exploited, potentially revealing your true IP address or allowing malicious actors to intercept your traffic. The very act of connecting to a VPN server can also be a distinguishing factor, making your traffic stand out from regular internet usage and potentially attracting unwanted attention.
Another crucial point often overlooked is that while a VPN masks your IP address from the external websites and services you visit, your Internet Service Provider (ISP) still knows that you are connecting to a VPN server and the duration of your connection. While they might not be able to see the specific content of your encrypted traffic, the fact that you are using a VPN can, in some contexts, raise red flags or make you a target for further scrutiny. Moreover, if you are not careful with browser configurations, cookies, and other tracking mechanisms, your true identity can still be pieced together even while using a VPN.
The cost factor is also a significant consideration. Reliable VPN services that offer decent speeds and a wide range of server locations typically come with subscription fees. While there are free VPNs available, these often come with their own set of drawbacks, including limited bandwidth, slower speeds, intrusive advertisements, and, most concerningly, the potential for data logging and even the injection of malware. The promise of “free” often comes at the cost of your privacy and security.
Finally, the complexity of properly configuring and using a VPN can be a barrier for many users. Ensuring that all traffic is routed through the VPN tunnel and preventing IP leaks requires careful configuration and constant vigilance. A simple misconfiguration can inadvertently expose your true IP address, rendering the VPN useless for anonymity purposes.
Given these significant limitations and potential vulnerabilities, relying solely on a VPN for true anonymity is akin to wearing a flimsy disguise in a world equipped with sophisticated surveillance technology. A more robust and trustworthy solution is needed for individuals who require a higher degree of privacy and protection from pervasive tracking and potential threats.
Understanding the Tor Network
Before diving deep into the solution for reliable anonymity, let refresh our mind on Tor. The Tor Network, often referred to as “The Onion Router.” offers a fundamentally different approach to online anonymity, one that moves beyond the single-hop connection of a VPN and embraces a decentralized, multi-layered architecture.
What is Tor?

At its core, Tor is a free and open-source software that directs internet traffic through a global, volunteer-operated network of relays. When you use Tor, your internet traffic is not sent directly to the destination server. Instead, it is routed through a series of randomly selected relays, each of which encrypts one layer of the data, much like the layers of an onion – hence the name. Each relay in the circuit only knows the IP address of the previous and the next relay, not the entire path. By the time your traffic reaches the final relay, known as the “exit node,” the origin of the traffic is effectively obscured, making it significantly more difficult to trace back to your original IP address.
The Security Promise of Tor
The inherent design of Tor offers several key advantages over traditional VPNs in terms of anonymity. The distributed nature of the network means there is no single point of failure or control. Unlike a VPN provider who can be compelled to hand over logs, the vast and decentralized Tor network makes it incredibly challenging for any single entity, including governments, to monitor or compromise the entire system. The multi-layered encryption ensures that even if one relay were compromised, the attacker would only gain access to a small, encrypted portion of the data and would not be able to trace the origin or the ultimate destination.
Furthermore, because Tor is a volunteer-run network, there is no central entity profiting from your data. The open-source nature of the software allows for public scrutiny and community-driven security audits, enhancing its transparency and trustworthiness. By bouncing your traffic through multiple, geographically diverse relays, Tor makes it significantly harder for websites and trackers to correlate your online activities and build a profile based on your IP address.
The limitations of Tor
However, even Tor is not without its limitations and potential flaws. The very process of routing traffic through multiple relays introduces latency, which can result in slower browsing speeds compared to a direct connection or even a VPN. This can make Tor less suitable for bandwidth-intensive activities like streaming or downloading large files.
Another potential concern lies with the exit nodes. These are the final relays in the Tor circuit through which your traffic exits onto the public internet. The exit node can see the unencrypted traffic destined for non-HTTPS websites. While your origin remains hidden, the traffic at the exit node is potentially vulnerable to eavesdropping if the website is not using encryption (HTTPS). While the vast majority of websites now use HTTPS, this remains a theoretical risk.
Additionally, while tracing traffic back to the original user through the entire Tor circuit is extremely difficult, sophisticated adversaries with significant resources and the ability to monitor a large portion of the network might theoretically be able to perform traffic correlation attacks, especially if there are weaknesses in the network or if users engage in activities that create unique traffic patterns.
Whonix: The Fortress of Anonymity

This is where Whonix enters the picture, offering a powerful and comprehensive solution that significantly enhances the anonymity and security provided by the Tor network by addressing some of its inherent limitations and introducing a robust layer of isolation.
What Exactly is Whonix?
Whonix (https://www.whonix.org/) is a free and open-source, Debian-based Linux distribution specifically designed for security and privacy. It achieves this by employing a unique and innovative architecture based on virtualization.
Understanding Virtual Machines (VMs)
To understand Whonix, it’s crucial to first grasp the concept of a Virtual Machine (VM). A VM is essentially a software-based emulation of a physical computer. It allows you to run an entire operating system (the “guest” OS) within another operating system (the “host” OS). The VM is isolated from the host system, meaning that any activities or software running within the VM are contained within its virtual environment and cannot directly affect the host system or other VMs. Popular virtualization software includes VirtualBox (https://www.virtualbox.org/) and VMware (https://www.vmware.com/).
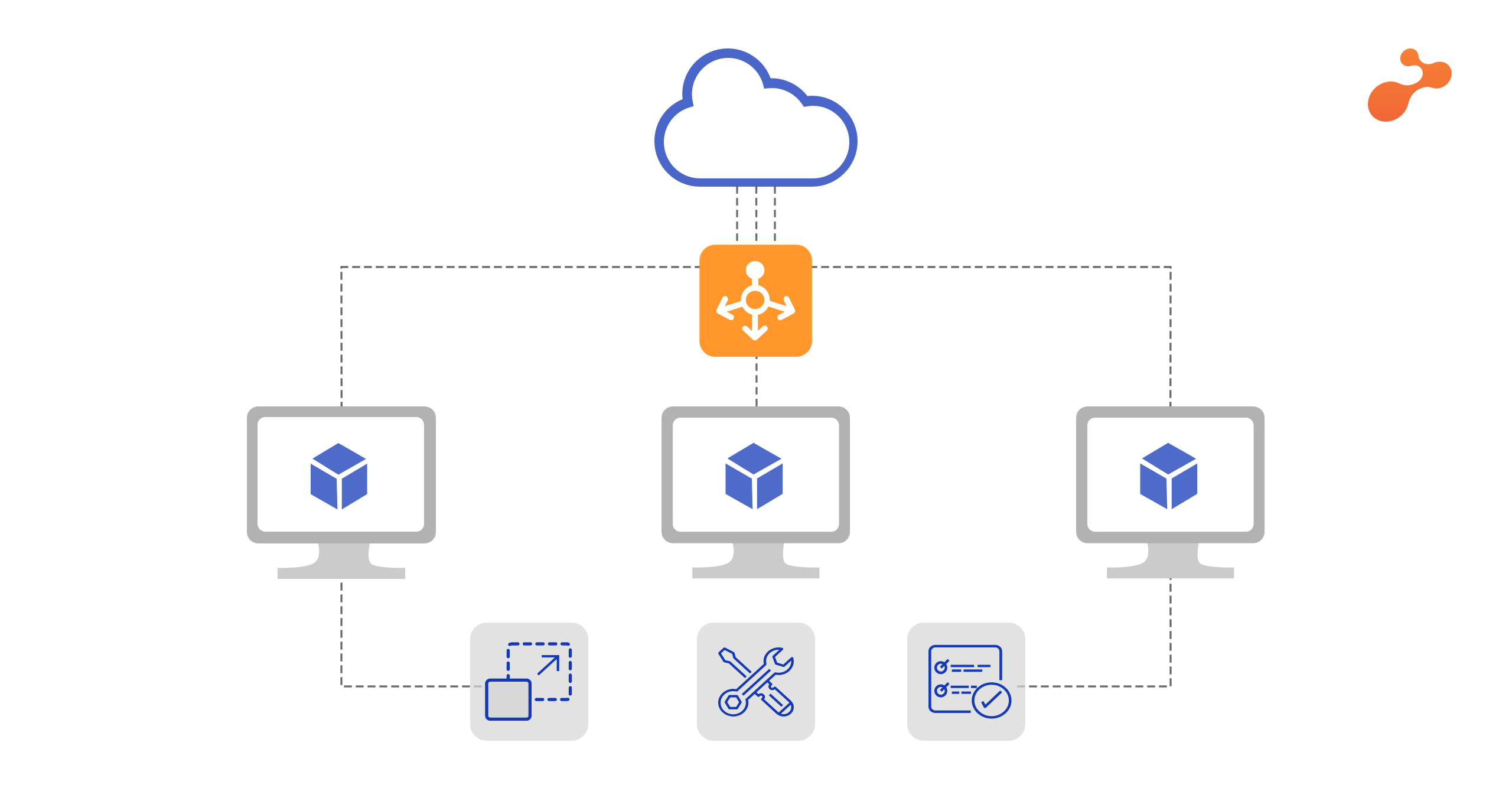
Whonix: A Two-Pronged Approach to Security
Whonix leverages this virtualization technology to create a highly secure and anonymous environment. It consists of two main virtual machines:
- The Workstation: This is the VM that you interact with directly. It contains your applications, web browser, and other tools you use for your online activities. Crucially, the Workstation is designed to have no direct network interface. It cannot directly access the internet.
- The Gateway: This VM acts as the sole gateway to the internet for the Workstation. It is responsible for establishing and maintaining a connection to the Tor network (https://www.torproject.org/). All traffic originating from the Workstation is forcibly routed through the Gateway and then through the Tor network.
This separation of functionalities into two isolated VMs is the cornerstone of Whonix’s enhanced security and anonymity. Here’s how it addresses the limitations of using Tor alone and provides significant advantages:
The Unbreakable Wall: Enhanced Security through Isolation
The most significant advantage of Whonix is the powerful isolation it provides. Because the Workstation has no direct network access, it is inherently protected from many types of attacks that could compromise your anonymity. For instance:
- IP Leaks: A common vulnerability when using Tor directly is the potential for applications or browser plugins to bypass the Tor proxy and directly connect to the internet, revealing your real IP address. In Whonix, this is virtually impossible because the Workstation simply has no way to establish a direct network connection. All network traffic, without exception, must pass through the Tor-enabled Gateway.
- Malware and Exploits: If the Workstation were to be compromised by malware or an exploit, the attacker would be confined to the isolated virtual environment. They would not have direct access to your host operating system or any other data outside of the Workstation VM. This significantly limits the potential damage and prevents the attacker from gaining access to your true identity or sensitive information stored on your host system.
- DNS Leaks: Domain Name System (DNS) leaks occur when your computer queries your ISP’s DNS servers instead of the DNS servers associated with the Tor network, potentially revealing your location. Whonix’s Gateway VM is configured to handle all DNS requests through Tor, preventing DNS leaks from the Workstation.
The Perfect Partnership: The Advantage of VMs + Tor
The combination of virtual machines and the Tor network creates a powerful synergy for anonymity:
- Forced Tor Usage: Whonix enforces the use of Tor for all network traffic originating from the Workstation. There is no way for applications to bypass Tor accidentally or intentionally. This ensures that your IP address is always masked by the Tor network.
- Anonymity at the Application Level: Because all applications within the Workstation are forced to use Tor, even applications that might not be explicitly configured to use a proxy will have their traffic anonymized. This provides a consistent level of anonymity across all your online activities within the Whonix environment.
- Multiple Layers of Defense: You have the inherent anonymity provided by the Tor network, coupled with the isolation and security provided by the virtual machine environment. This layered approach significantly increases the difficulty for adversaries to deanonymize you.
Simplicity and Power: Use Cases for Whonix
Despite its sophisticated underlying architecture, Whonix is designed to be relatively user-friendly. It comes pre-configured with Tor and the necessary network settings, making it easier for users to achieve a high level of anonymity without requiring extensive technical knowledge. You can download Whonix from its official download page: https://www.whonix.org/wiki/Download. The website also provides comprehensive documentation (https://www.whonix.org/wiki/Documentation) to guide users through the installation and usage process.
Whonix is particularly valuable in various use cases where strong anonymity is crucial:
- Journalists and Whistleblowers: Protecting the identity of sources and ensuring secure communication is paramount for investigative journalists and whistleblowers. Whonix provides a secure environment for these sensitive activities.
- Human Rights Activists: Individuals working in oppressive regimes or advocating for human rights often face significant risks. Whonix can help them communicate securely and anonymously, protecting them from surveillance and retaliation.
- Privacy-Conscious Individuals: For anyone who values their online privacy and wants to minimize their digital footprint, Whonix offers a robust and reliable solution.
- Circumventing Censorship: In regions where internet access is restricted or certain websites are blocked, Whonix can be used to bypass censorship and access information freely.
- Security Researchers: Whonix provides an isolated environment for testing potentially malicious software or conducting security research without risking their main system.
The Power of Whonix’s Isolation in Detail
The isolation provided by Whonix’s dual-VM architecture is its most compelling security feature. Let’s delve deeper into why this isolation is so powerful:
Imagine your regular computer as a single room. Everything you do online happens in this room. If there’s a security vulnerability in one part of the room (an application, your operating system), an attacker could potentially gain access to the entire room and everything within it, including your personal data and your true identity.
Now, imagine Whonix as a building with two separate, heavily fortified rooms. The Workstation is one room, and the Gateway is the other. The Workstation, where you do all your work, has no doors or windows leading directly outside. The only way anything can leave or enter the Workstation is through a secure, controlled portal to the Gateway room. The Gateway room, in turn, has a secure connection to the outside world via the Tor network.
This architectural design offers several critical security advantages:
- Preventing Real IP Address Exposure: Because the Workstation has no network interface, it simply cannot communicate directly with the internet. Any attempt by an application or process within the Workstation to access the network will be forcibly routed through the virtual network interface connected solely to the Gateway VM. The Gateway then ensures that all traffic is anonymized through Tor before it leaves the virtual environment. This eliminates the risk of accidental or malicious IP leaks from within the Workstation.
- Containment of Compromises: If the Workstation is somehow compromised (e.g., through a browser exploit or malware), the attacker’s access is limited to the isolated Workstation VM. They cannot directly access the host operating system, other applications on the host, or any sensitive data stored outside of the Workstation. This containment significantly reduces the severity of a potential security breach.
- Mitigation of Side-Channel Attacks: While Tor itself provides strong anonymity at the network level, certain sophisticated side-channel attacks could potentially try to correlate activity within your local system with your Tor traffic. Whonix’s isolation makes such attacks significantly more difficult by separating the application layer (Workstation) from the network layer (Gateway).
- Simplified Security Management: By centralizing the Tor connection within the Gateway VM, Whonix simplifies the security configuration. You only need to ensure that the Gateway is properly configured to use Tor. The Workstation inherently benefits from this secure connection without requiring individual application-level configurations.
- Reproducible and Auditable Environment: Because Whonix is based on open-source software (https://github.com/Whonix) and its architecture is well-documented, it allows for public scrutiny and security audits. This transparency enhances trust and allows the community to identify and address potential vulnerabilities.
In conclusion, while VPNs can offer a basic level of privacy by masking your IP address, they fall short of providing true anonymity and come with their own set of security risks and limitations. The Tor network offers a more robust approach to anonymity through its decentralized and multi-layered routing. However, even Tor has its potential weaknesses. Whonix builds upon the strengths of Tor by introducing a powerful layer of isolation through its unique dual-VM architecture. By separating the workstation from the Tor gateway, Whonix effectively eliminates the risk of IP leaks, contains potential compromises, and provides a significantly more secure and anonymous online environment. For individuals who prioritize true anonymity and security, moving beyond the illusion of VPNs and embracing the robust protection offered by Whonix is a crucial step towards reclaiming their digital privacy. It is a testament to the power of free and open-source software in providing genuine solutions for navigating the increasingly complex and surveilled digital world.