Imagine a thriving startup, fresh off a successful funding round, deploying updates every few hours to keep pace with user demand. One morning, a frantic Slack alert lights up the channel: sensitive customer data has surfaced on a dark web forum. The root cause? A misconfigured CI/CD pipeline allowed an attacker to inject malicious code during the automated build process. This isn’t a far-fetched scenario—it’s a real-world consequence of overlooking security in systems designed for speed. As organizations prioritize continuous integration and delivery to accelerate software releases, the need to harden pipeline security becomes urgent, not optional.
Secure Code Practices: The Foundation of Trustworthy Pipelines
Security starts in the code itself. Developers must treat applications as living entities that evolve with every commit, not static assets. Static application security testing (SAST) tools like SonarQube should scan repositories during pull requests, flagging vulnerabilities such as SQL injection risks or insecure dependencies. Dynamic testing tools like OWASP ZAP can simulate attacks on running applications in staging environments, revealing runtime flaws.
For entrepreneurs and remote workers, integrating these tools reduces the risk of costly post-deployment fixes. Educators might emphasize peer code reviews as part of curriculum—teaching teams to identify logic gaps or hardcoded credentials. Comprehensive testing isn’t just a developer’s responsibility; it’s a collaborative effort. Consider a developer who hastily merges a feature branch without checking outdated libraries. If the pipeline lacks SAST integration, that oversight could expose the entire system to breaches.
![]()
Infrastructure as Code: Balancing Automation and Accountability
Infrastructure as code (IaC) tools like Terraform and AWS CloudFormation abstract server management into version-controlled templates. But when these templates contain misconfigurations—such as open ports or overly permissive IAM policies—they create vulnerabilities at scale. Teams should treat IaC files like application code: scan them with tools like Checkov or TFSec, which parse templates for insecure patterns, and enforce strict change management before deployment.
Remote workers managing cloud resources must avoid the temptation to “quick fix” IaC files without peer review. Freelancers taking on DevOps tasks should pair IaC with drift detection systems to ensure deployed environments match their source templates. For educators, creating labs around IaC security teaches students to spot misconfigurations before they reach production.
Secrets Management: Protecting the Keys to the Kingdom
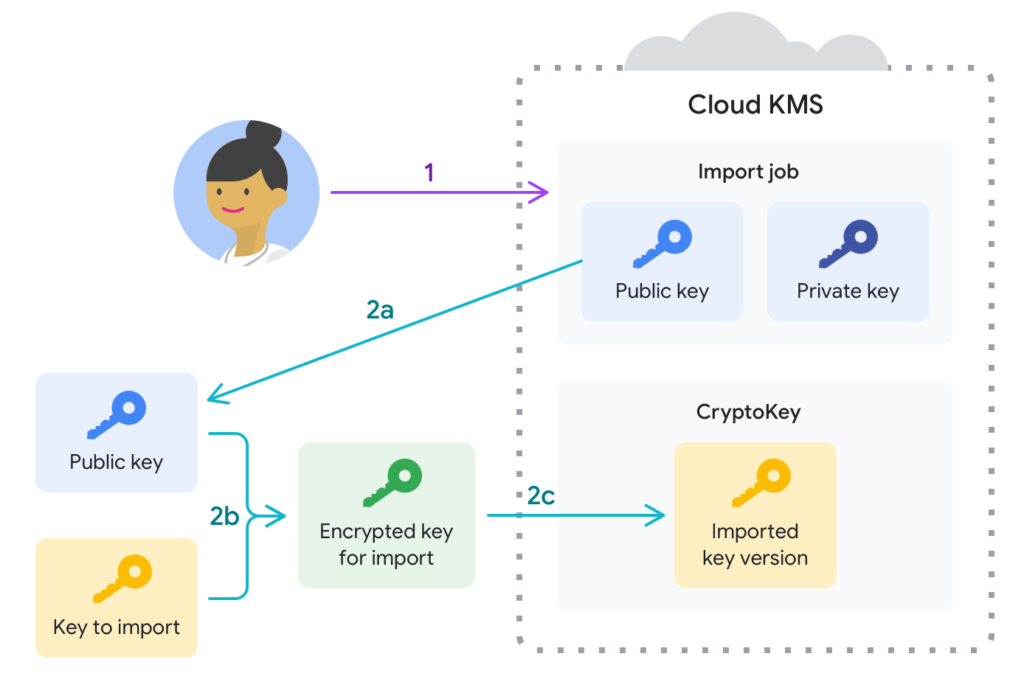
Hardcoded API keys, database passwords, and SSH tokens are time bombs in source code. A single leaked credential can grant attackers unrestricted access to critical systems. Use centralized secret stores like HashiCorp Vault or Azure Key Vault, which inject credentials at runtime rather than storing them in plain text. Rotate secrets regularly and restrict access to specific pipeline stages.
Consider a scenario where a developer stores a production database password in a GitHub Actions workflow. If the repository is publicly accessible, that credential becomes a liability. By integrating secret management tools, organizations ensure credentials never appear in logs or code history. Entrepreneurs should budget for these tools as part of their security infrastructure, while remote workers must verify that secrets aren’t exposed in local environments.
Access Control: Guarding the Gates with Precision
In a remote team with 30 members, granting unrestricted access to pipeline tools like Jenkins or GitLab isn’t just careless—it’s risky. Role-based access control (RBAC) ensures developers can’t approve their own merges, QA engineers can’t modify deployment scripts, and freelancers only interact with designated sandboxes. Tools like AWS IAM or Azure AD enable granular permissions tied to user identities.
A professional working in a regulated industry, such as healthcare or finance, might need compliance certifications like SOC 2 or HIPAA. RBAC provides audit trails showing who accessed what, making compliance checks smoother. Educators can demonstrate RBAC by assigning students roles in a simulated deployment environment, reinforcing the principle of least privilege.
Monitoring and Logging: The Art of Seeing the Unseen
In 2023, a SaaS company detected a breach by analyzing abnormal timestamps in their deployment logs. Continuous monitoring tools like Datadog or Grafana track pipeline activity, while centralized logging systems like ELK Stack aggregate data for forensic analysis. These systems should trigger alerts for suspicious behavior, such as a deployment initiated from an unauthorized IP address or a sudden spike in failed builds.
For developers, monitoring isn’t just about catching attacks—it’s a feedback loop for improving pipeline reliability. Freelancers can use logging to debug environment-specific issues without compromising sensitive data. Regularly review logs to identify patterns that indicate tool misuse or configuration drift.
Testing Strategies: Beyond Unit Tests
A pipeline that runs unit tests but skips integration checks is like a house with a sturdy front door but open windows. Security testing should span multiple layers:
- Unit tests verify individual components.
- Integration tests validate system interactions.
- Penetration tests simulate real-world attack scenarios.
Tools like BDD-Security allow behavior-driven testing for security features. Educators can design exercises where students breach a deliberately vulnerable system, learning to anticipate threats. Developers should automate these tests to run at every stage, ensuring no commit slips through unchecked.
Compliance as Code: Embedding Governance into the Pipeline
Manual compliance checks slow down pipelines and introduce human error. Tools like InSpec or Open Policy Agent (OPA) let teams write policies that test infrastructure against frameworks like GDPR or CIS benchmarks. These policies run during deployment, blocking non-compliant resources from being created.
A professional in a regulated field might use compliance as code to enforce encryption standards across all cloud resources. For entrepreneurs, this approach reduces the cost of audits while providing assurance to stakeholders. Remote workers should ensure their local setups meet compliance standards before pushing changes.
Securing CI/CD Tools: Defense in Depth
Popular CI/CD platforms like Jenkins, GitLab, and Azure DevOps are frequent targets. Keep tools updated to patch known vulnerabilities, and disable unused plugins or features. For example, Jenkins’ Security Advisories page lists critical fixes that teams must apply promptly.
Self-hosted pipelines require extra vigilance. If a freelancer configures a CI server on a personal VPS without hardening it, they risk exposing the entire pipeline. Use containerization with Docker Bench to scan hosts for security gaps.

Incident Response: Preparing for the Inevitable
No system is impervious. When a breach occurs, a pre-defined incident response playbook becomes a lifeline. Outline steps for:
- Isolating compromised pipeline stages.
- Notifying relevant stakeholders.
- Restoring from verified backups.
Conduct tabletop exercises where developers and operations teams simulate breach scenarios. Remote workers should know how to escalate issues even if disconnected from internal tools. Post-incident analysis should feed findings back into the pipeline, closing gaps like a leaky IAM role or unpatched tool.
Future-Proofing Security: The Role of AI and Automation
Emerging trends like AI-driven threat detection are reshaping pipeline security. Tools like Snyk use machine learning to predict vulnerabilities in dependencies. In 2024, 45% of organizations plan to adopt predictive security analytics, according to a Gartner report.
Educators should introduce students to AI’s ethical implications in security—how it can both protect systems and be weaponized by attackers. Freelancers can leverage open-source AI tools to audit code quality and flag risky patterns.
Collaboration: The Human Element in Automated Pipelines
Security isn’t a solo endeavor. Encourage cross-functional teams to share ownership. For instance, a QA engineer might catch an authentication flaw during testing, while a DevOps engineer hardens the build server. Regular security training keeps everyone aligned—whether in an office or a home workspace.
A remote worker in Brazil and a developer in Japan should have the same security protocols enforced in their environments. Use tools like GitHub Security to standardize practices across distributed teams.
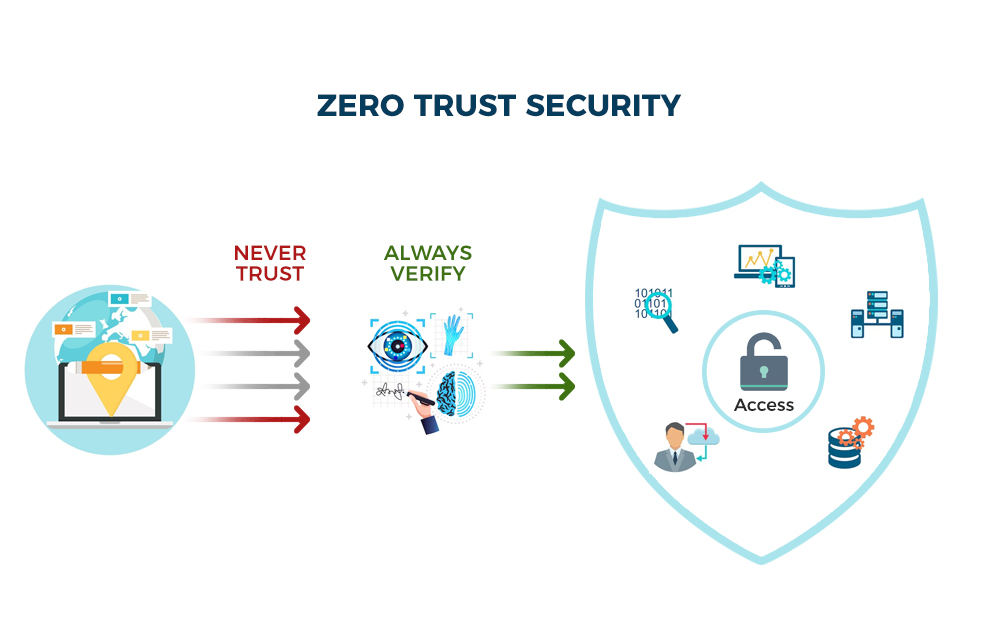
Zero Trust: The New Paradigm
Traditional pipelines assume trust within the network. Zero Trust architectures, however, verify every request. For example, a deployment script shouldn’t trust a container image just because it’s in a private registry—scan it for malware before execution. Tools like Notary sign and verify artifacts at each stage.
Entrepreneurs might partner with security consultants to model Zero Trust principles tailored to their business. Developers should integrate attestation tools like Sigstore to sign code commits cryptographically.
Immutable Infrastructure: Building Castles on Solid Ground
Mutable infrastructure—where servers are updated in place—creates drift and vulnerabilities. Immutable infrastructure, like Kubernetes’ rolling updates, replaces assets entirely with new, verified versions. This approach limits exposure to unauthorized changes.
A professional managing a high-traffic e-commerce site could use immutable pipelines to ensure every update passes security gates before deployment. Freelancers should advocate for immutable practices when advising clients on cloud migration.
Conclusion: Security as a Journey, Not a Destination
Creating a secure CI/CD pipeline isn’t a one-time setup. It’s an evolving practice requiring vigilance, collaboration, and a willingness to adapt. Whether you’re an educator shaping the next generation of DevOps engineers or a remote worker deploying code from a café, security is a collective responsibility.
By weaving these practices into daily workflows, teams transform pipelines from potential liabilities into fortified conduits for innovation. The difference between a resilient system and a catastrophic breach often lies in the smallest details—a missed permission check, an outdated tool, an overlooked log entry. Guard these like treasure, and your pipeline will become a beacon of trust in a landscape where trust is scarce.




